A large-scale Coinbase phishing attack poses as a mandatory wallet migration, tricking recipients into setting up a new wallet with a pre-generated recovery phrase controlled by attackers.
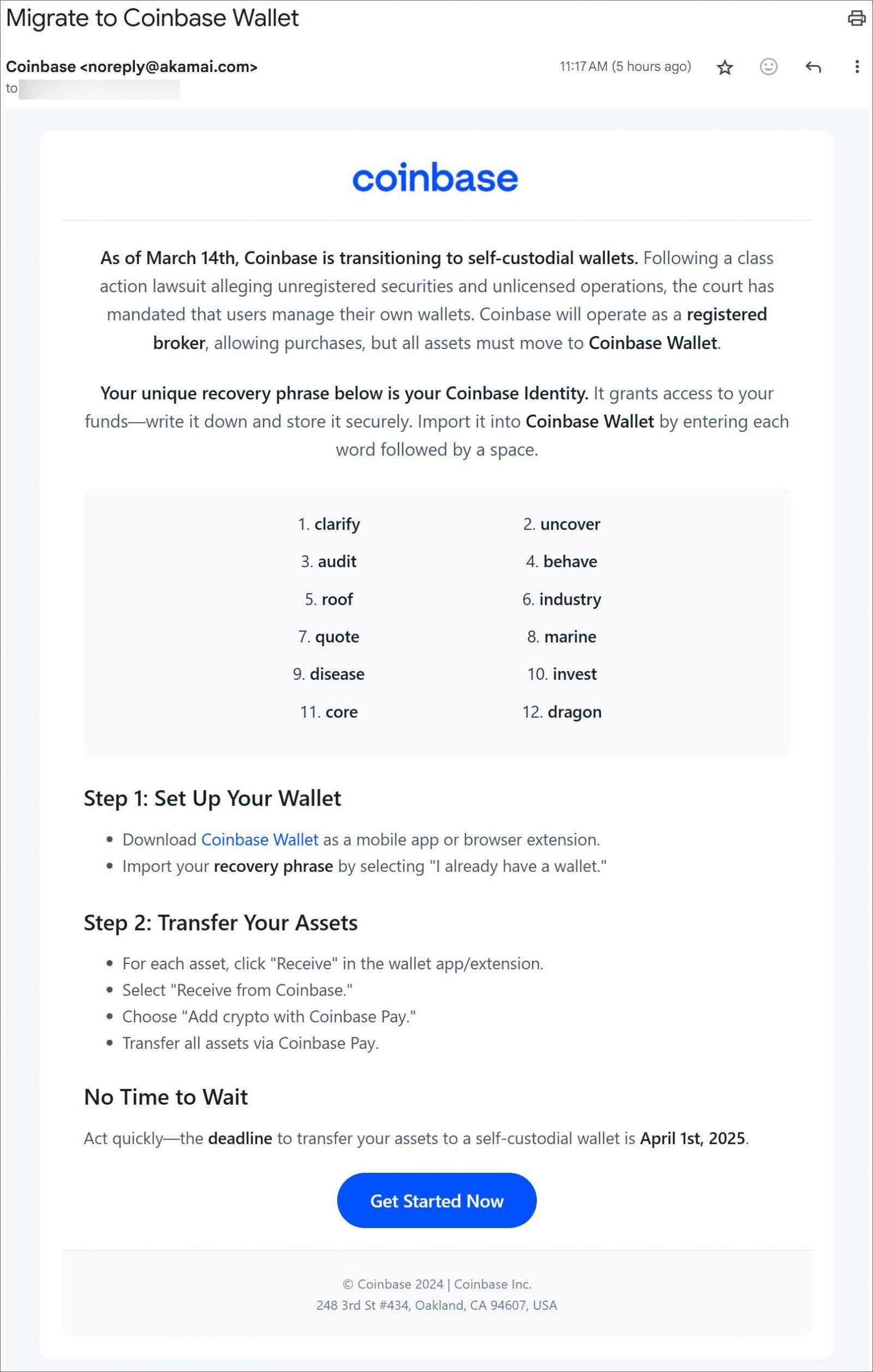
The emails have a subject of “Migrate to Coinbase Wallet” and state that all customers must transition to self-custodial wallets. The email also provides instructions on how to download the legitimate Coinbase Wallet.
“As of March 14th, Coinbase is transitioning to self-custodial wallets. Following a class action lawsuit alleging unregistered securities and unlicensed operations, the court has mandated that users manage their own wallets,” reads the Coinbase phishing email.
“Coinbase will operate as a registered broker, allowing purchases, but all assets must move to Coinbase Wallet.”
“Your unique recovery phrase below is your Coinbase Identity. It grants access to your funds—write it down and store it securely. Import it into Coinbase Wallet by entering each word followed by a spa
Source: BleepingComputer
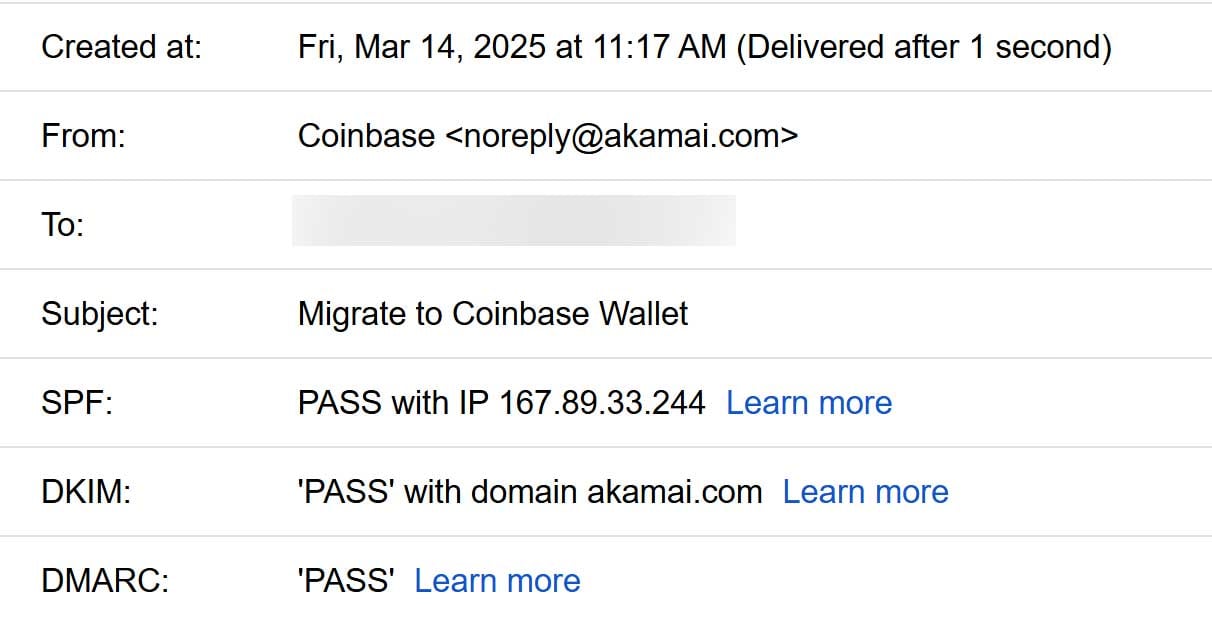
The email claims to be from Coinbase but has a reply address of [email protected]. It is also sent from the IP address 167.89.33.244, which is a SendGrid IP address that resolves via DNS to o1.soha.akamai.com.
As the email appears to have been sent directly through SendGrid and what appears to be Akamai’s account, it passes the SPF, DMARC, and DKIM email security checks, bypassing spam filters on many accounts.
Source: BleepingComputer
BleepingComputer contacted Akamai to ask if one of their SendGrid accounts had been compromised and was sent the following statement.
“Akamai is aware of reports regarding a potential phishing scam targeting Coinbase users that involves an Akamai email domain. We take information security very seriously and are actively investigating the matter,” Akamai told BleepingComputer.
“Phishing scams remain a prevalent cyber threat, and we urge all users to exercise caution if they receive unsolicited emails, especially those requesting personal or account information. If you suspect that an email may be a phishing attempt, please treat it as such and avoid clicking any links or providing any sensitive information.”
“We are working to address the situation and will continue to monitor and mitigate any related risks. In the meantime, we recommend heightened vigilance to help protect your personal information.”
A clever crypto phishing campaign
What makes this phishing campaign stand out is that there are no phishing links present within the email, and all links go to Coinbase’s legitimate Wallet page.
Instead, the phishing email includes a recovery phrase, which the phishing email says should be used to set up your new Coinbase Wallet.
Recovery phrases, also known as “seeds,” are a series of words that function as a human-readable version of a cryptocurrency wallet’s private key.
Anyone who knows this recovery phrase can import the wallet onto their own devices, allowing them to steal any cryptocurrency and NFTS stored within it.
While most cryptocurrency phishing scams attempt to steal your recovery phrase, which is then used by the attacker to steal your funds, this one acts in reverse.
This phishing email is very clever, as instead of stealing your phrase, they are giving you one that is already known and controlled by the attacker.
Once a user sets up a new wallet with that phrase and transfers funds into it, all of the assets will now be available to the threat actor who can then transfer them to another wallet they control.
Coinbase is aware of the scam, pointing BleepingComputer to a post on X where saying they will never recovery phrases to customers.
“Reminder: Beware of recovery phrase scams,” Coinbase posted on X.
“We’re aware of new phishing emails going around pretending to be Coinbase and Coinbase Wallet. We will never send you a recovery phrase, and you should never enter a recovery phrase given to you by someone else.”
For anyone who fell for this scam, if the funds are still available on the newly created wallet, you should be quick to transfer them back out to your own before they are stolen by the threat actors.
While the rule has always been to never share your recovery phrase with another person or a website, it should now be expanded to never use a recovery shared with you via emails and websites, as they are likely used to steal your cryptocurrency.


